Network Segmentation & SD-WAN
The Target breach highlighted the need to segment networks and isolate traffic. Adding software-defined networking capabilities to the WAN can help.

The Target breach has become a cautionary tale for IT personnel in large enterprises. That’s a shame, because Target, along with other big-box retailers and millions of customers, would have been spared the losses and the grief had it not been for one very outdated aspect of the typical enterprise architecture: the lack of network segmentation in the WAN.
With the ability to segment networks and isolate traffic, enterprises would be able to prevent attacks that quickly evolve into damaging mega breaches that happen when attackers access data across different segments of an enterprise’s network. Furthermore, the Target incident showed that the breach does not need to come from inside a company’s own network. Business partners can have their systems compromised, and then have that infection spread to others’ data as well.
Network segmentation benefits
Enterprises need a set of safeguards to ensure that sensitive data remains secure, and that potentially compromised network edges and business partner data can be quarantined and scrubbed at a moment’s notice. For example, when you integrate a supplier onto the network, you want to isolate it from all sensitive corporate information, such as customer data.
Figure 1: 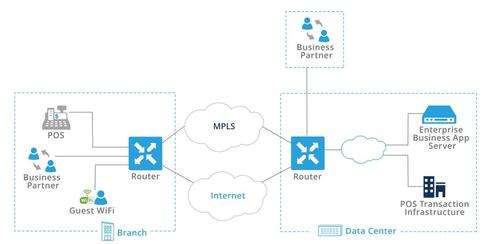
Network segmentation provides additional benefits including:
Segmentation of lines of businesses, regardless of location
Separation of guest WiFi access for clients and partners
Isolating on-demand development and test labs that span multiple locations
Making it easier for compliance and audits such as PCI-DSS and HIPAA
Multi-tenant and B2B partners
Digital signage and DVR services
Perhaps most assuring to CIOs and IT is the ability to create different privileges for BYOD based on users, devices, and location-based policies. This represents an incredibly simple fix to the headaches and potential security leaks that result from BYOD policies becoming abused by careless employees.
Cross-site traffic segmentation difficulties
Segmentation isn’t difficult within a site (using VLANs), but the isolation is lost once the traffic exits the site and enters the WAN. That is, the isolation cannot be maintained across the enterprise, leaving the possibility for security breaches. In order to properly extend segmentation throughout the network, the relevant identifying information must be carried to all points in the network.
Legacy networks provide two different solutions to this problem; unfortunately, both are insufficient. The first approach is to define a grouping policy on a single device and enforce it at every point in the network, which is what you see in VRF Lite and hop-by-hop VRFs. In addition to lacking much-needed scalability, there are too many points in the network to enforce that policy; head-end becomes unmanageably complex and change control becomes extremely difficult.
The other approach is to define the policy at the network edge and carry the segmentation information in the data traffic, as in MPLS Layer 3 VPNs, for example. Unfortunately, this becomes complex and cost-prohibitive.
SD-WAN and segmentation
What companies need is a robust network infrastructure that integrates routing, security, centralized policy, and orchestration to provide a secure network with innate capabilities for end-to-end segmentation. Adding software-defined networking capabilities to the WAN creates the SD-WAN, which addresses this problem. The SD-WAN can not only segment information, but also communicate it to all relevant points in the network without external mechanisms or additional protocols, which simplifies network design.
Figure 2: 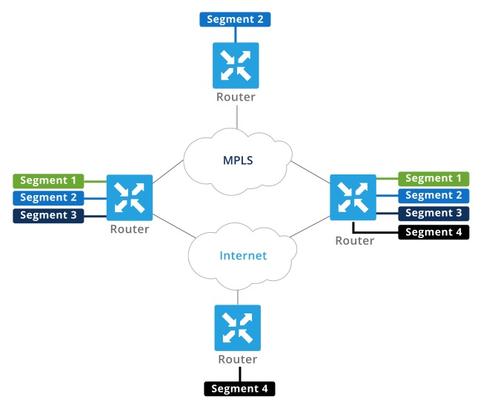
An SD-WAN also provides the enterprise with:
Creation of end-to-end network segmentation over an existing network, but without modifying any devices in the path
Enforcement of segmentation-based policies (for example, guest WiFi traffic should take the least expensive circuit, while preserving high-SLA circuits for revenue-generating traffic)
Control of which segments gain access based on location, thereby preventing attacks on remote sites
Enforcement of network policies based on segments (for example, traffic from unknown BYOD devices routed through a DMZ-scrubbing site before allowing access to the network)
Enforcement of network topologies based on segments (for example, segments with interactive voice/video can go site-to-site, versus certain other segments that are purely hub-and-spoke)
The idea of segmenting networks end-to-end provides something that the networking industry has been thinking of for several years, but it had been too complex to implement. However, the sophistication and unpredictability of today’s cyberattacks mean that firewalls and encryption alone are not enough to keep enterprise data safe -- network segmentation has to be an integrated part of that strategy.
About the Author
You May Also Like





